RandomKeygen is a free mobile-friendly tool that offers randomly generated keys and passwords you can use to secure any application, service or device. KEY RandomKeygen - The. The Wireshark WPA Pre-shared Key Generator provides an easy way to convert a WPA passphrase and SSID to the 256-bit pre-shared ('raw') key used for key derivation. Type or paste in your WPA passphrase and SSID below. Wait a while. The PSK will be calculated by your browser. Javascript isn't known.
CD Key Generator
'CD Key Generator' generates up to 4,000,000 unique key combinations and 5,000,000 non-unique key combinations.Generate random alpha, numeric, or both, CD keys for software distribution and registration. A maximum key length of 48 characters may be generated. Keys may be generated in multiple character or numerical formats including decimal, binary, hexadecimal and octal.
- Publisher: Jedisware, LLC
- Home page:www.jedisware.com
- Last updated: December 4th, 2012
Motacore Key Generator Lite
Motacore Key Generator Lite enables you to easily generate CD/DVD/Product keys. It also integrates with your VB.NET and C# applications providing an easy solution for providing Demo applications with the ability to unlock them with a product key. Motacore Key Generator Lite integrates into your .NET applications providing you with an easy and secure way to enable demo versions
- Publisher: Motacore
- Home page:www.motacore.com
- Last updated: October 30th, 2017
Abluescarab Software CD-Key Generator
The Abluescarab Software CD-Key Generator will help you generate random CD keys for use in your shareware products. You can choose letters, numbers, or both. You can also pick whether or not to use lowercase letters.Main Features:- Choose between letters, numbers, or both- Choose whether or not to use lowercase letters- Choose how many sections (separated by dashes) there are
- Publisher: Abluescarab Software
Pre Shared Key
WiFi Password Key Generator
WiFi Password Key Generator is exactly what its name suggests: a program that helps you create Wireless WEP and WPA/WPA2 keys on your Windows PC. These types of keys are necessary when a modem or a router requires you to provide WEP or WPA keys during a Wireless security setup.
That’s why a free 29-point inspection with one of our service technicians is never a bad idea. Auto tune up specials near me. For many years, a vehicle tune-up service involved an engine inspection and, if necessary, a replacement carburetor and sparkplugs. And if your vehicle was made before 2000, a tune-up service remains the same.However, if your vehicle was made after the year 2000, it’s unlikely to have a carburetor.
- Publisher: SecurityXploded
- Home page:securityxploded.com
- Last updated: February 27th, 2017
Userbase
Userbase is designed to allow the software author to easily process and track orders, users, products and registration information.Pull your software orders from your email through the embedded email client and the program can parse your orders into the database.
- Publisher: Lazy Dog Software
- Home page:www.lazydogsoftware.com
- Last updated: March 4th, 2011
Key generator free
Key Generator Free will help you generate passwords. As some websites and applications will require character specifications to strengthen your password security, this application lets you select some of the usual requirements. In this regard, you may specify password length, use of upper and lower case, special characters and numbers.
- Publisher: PCTips3000
- Last updated: August 30th, 2011
Advanced ID Creator Enterprise
Create and print professional ID cards and badges instantly! Advanced ID Creator allows you to create great looking id cards. Use the wide variety of tools to add text, graphics, shapes, barcodes, shadows and other effects to your design.
- Publisher: Xpress Software Inc.
- Last updated: July 21st, 2015
Inno Key Generator
If you're a user of Inno Setup then this freeware application will allow you to force users to enter their registration credentials before the installation can proceed.The download includes a key generator, validation DLL for inclusion in your scripts, a help file and sample script (actually the same script used for the installation of IKG itself).
- Publisher: MJ Freelancing
- Home page:www.mjfreelancing.com
- Last updated: November 15th, 2009
Serial Key Generator
Serial Key Generator is a program to help developers generate serial numbers for applications. You can generate serial keys using a custom number of columns and characters per column. The sequence of numbers/digits can be defined in the application. The output can be saved as CSV or TXT documents.
PC Games Download Full Version. Cooking Games Free Download For PC!Our free Cooking Games are downloadable for windows 7/8/8.1/10/xp/vista.We provide you with the finest selection of pc games free download that will bring you lots of fun! Play PC Cooking games featuring burgers, desserts and ice cream. Try before you buy! Free download cooking games full version for windows 8 4. GameTop offers you amazing collection of cooking games to download and play at no cost. For over 10 years we give unique opportunity to all gamers around the word to enjoy over 1000+ downloadable PC games for free. All our cooking games are 100% unlimited full version games with fast and secure downloads, no trials and not time limits. Download and play free Cooking Games. Serve up delicious meals in the best games featuring cooking and kitchens! Become a chef and serve up delicious meals to happy diners as you play free Cooking Games. Try before you buy! 8 Cooking Trip Collector's Edition 9 Katy and Bob: Cake Cafe Collector's Edition.
- Publisher: VCL Examples
- Home page:skgenerator.vclexamples.com
- Last updated: September 3rd, 2014
Elcomsoft Wireless Security Auditor
Audit security of your wireless networks and recover WPA/WPA2 with patent-pending GPU acceleration technology that speeds up password recovery if one or more compatible NVIDIA or ATI video cards are installed.
- Publisher: ElcomSoft Co. Ltd.
- Home page:www.elcomsoft.com
- Last updated: September 24th, 2015
Sticky Password
Sticky Password is a password manager that can save all your login IDs, passwords, addresses, credit card numbers, and auto-fill them on web forms. Its password generator lets you create strong passwords. You can also use it to store your passport data, licenses, and other sensitive information.
- Publisher: Lamantine Software
- Home page:www.stickypassword.com
- Last updated: June 14th, 2018
HashCalc
Fast calculator to compute hash, checksum, HMAC values for file, text and hex string. Supports MD2, MD4, MD5, SHA1, SHA2, RIPEMD160, PANAMA, TIGER, CRC32, ADLER32 algorithms and the hash used in eMule and eDonkey (eDonkey2000, ed2k) tools.
- Publisher: SlavaSoft Inc.
- Home page:www.slavasoft.com
- Last updated: March 6th, 2007
Access Manager
Access Manager is a FREE software solution that keeps all your passwords in one, simple to use list. It offers fast, easy and secure password management.One 'Master Password' is all that is needed to access all your passwords and private information.
- Publisher: Citi-Software Ltd
- Home page:www.AccessManager.co.uk
- Last updated: September 15th, 2010
Hybrid
Hybrid encrypts and decrypts files for storage on your computer. It uses the well known Blowfish encryption algorithm with 448 bit encryption. Hybrid offers an easy to use interface with drag and drop support and integrates into the Windows shell.
- Publisher: Selur
- Home page:www.selur.de
- Last updated: June 11th, 2008
eBook Maestro FREE
A very affordable tool for making ebooks, it has many wizards that help the user to make a huge variety of files in little time and with less effort. It is compatible with many other applications such as flash, java or video files, among others. Can protect the content of the ebook and can add trial limitations. It can be a very powerful tool if the user dedicates it enough time to learn it.
- Publisher: eBookMaestro.com
- Home page:www.ebookmaestro.com
- Last updated: March 2nd, 2008
Text Paster
Text Paster is a program for instantly pasting into input fields in practically any program simple or formatted (RTF) text that has been pre-defined by you: standard phrases, greetings, generic replies, the current date and time, letter and document templates, e-mail addresses, website addresses, usernames, passwords, text fragments selected on your screen, clipboard contents, and much more.
- Publisher: ATNSOFT
- Home page:www.atnsoft.com
- Last updated: January 8th, 2016
abylon KEYSAFE
The abylon KEYSAFE is a simply password manager to manage all your secret data. You need only one password or alternatively an USB Stick, CD, chip card or certificate as “keys”. The stored data can simply pull with the mouse into the appropriate fields of the Browsers or dialogue (Drag&Drop). With abylon KEYGENERATOR the software also offers a random password generator.
- Publisher: abylonsoft - Dr. Thomas Klabunde
- Home page:www.abylonsoft.com
- Last updated: July 2nd, 2018
Secure Password Manager
Do you have too many passwords, which expire on different dates, are subject to different rules, or are managed with different tools? This complexity creates problems, like forget your passwords.Secure Password Manager is the right solution to manage your passwords.
- Publisher: securekit.net
- Last updated: August 13th, 2012
How to Add a New Pre-Shared Key

Wpa Pre Shared Key
If you are using pre-shared keys, you must have one pre-shared key for every policy entry in the ipsecinit.conf file. If you add new policy entries while IPsec and IKE are running, the in.iked daemon can read in new keys. This procedure assumes the following:
The in.iked daemon is running
The interface that you want to protect with IPsec is an entry in the /etc/hosts file on both systems, for example:
You have added a new policy entry to the /etc/inet/ipsecinit.conf file on both systems. For example, the entry on enigma looks something like the following:
For example, the entry on ada looks something like the following:
You have created a rule for the interface on ada in the /etc/inet/ike/config file on both systems. For example, the rule on enigma looks something like the following:
For example, the rule on ada looks something like the following:
Note –All arguments to auth_method must be on the same line.
Infected mushroom pusher vst crack. On the system console, become superuser or assume an equivalent role.
Note –Logging in remotely exposes security-critical traffic to eavesdropping. Even if you somehow protect the remote login, the total security of the system is reduced to the security of the remote login session.
Check that the in.iked daemon permits you to change keying material.
You can change keying material if the command returns a privilege level of 0x1 or 0x2. Level 0x0 does not permit keying material operations. By default, the in.iked daemon runs at the 0x0 level of privilege.
If the in.iked daemon does not permit you to change keying material, kill the daemon. After killing the daemon, restart the daemon with the correct privilege level.
For example,
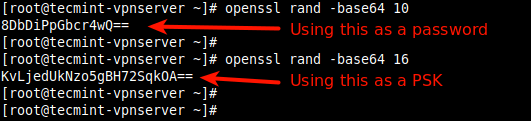
Generate random keys and combine the output to create a key of 64 to 448 bits.
On a Solaris system, you can use the od command.
For an explanation of the command, see How to Generate Random Numbers and the od(1) man page.
By some means, send the key to the administrator of the communicating system.
You are both going to add the same pre-shared key at the same time.
Add the new keying material with the add preshared subcommand in the ikeadm command mode.
id-type
The type of the id.
id
IP address when id-type is IP.
mode
The IKE mode. main is the only accepted value.
key
The pre-shared key in hexadecimal format.
For example, on host enigma, you add the key for the new interface, ada, 192.168.15.7
On host ada, the administrator would add the identical key, as in:
Note –A message of the form Error: invalid preshared key definition indicates that you gave incorrect arguments to the add preshared command. You might have mistyped a parameter. You might have omitted a parameter. Retype the command correctly to add the key.
Exit the ikeadm command mode.
On each system, lower the privilege level of the in.iked daemon.
On each system, activate the ipsecinit.conf file to secure the added interface.
Note –Read the warning when you execute the command. A socket that is already latched, that is, the socket is in use, provides an unsecured back door into the system.
On each system, read in the new rules by using the ikeadm command.
A sample of the new rules for ada and enigma are at the start of the procedure. Because the rules are in the /etc/inet/ike/config file, the name of the file does not have to be specified.
Little snitch 3.6.1. To ensure that IKE pre-shared keys are available at reboot, edit the /etc/inet/secret/ike.preshared file.
Jul 24, 2018 Auto-Tune Evo VST is an audio plugin specifically created for this type of situations. Since it is a VST plugin, it requires a compatible host before its functions can be accessed. Once set up, it allows musicians to apply pitch correction onto their tracks and make sure the resulting sounds are smooth and clear. Select Version Auto-Tune Pro 9.0.1 Auto-TuneProPCv9.0.1.zip Auto-Tune Pro is the most complete and advanced edition of Auto-Tune for Windows PC. It includes both Auto Mode, for real-time pitch correction and effects, and Graph Mode, for detailed pitch. May 17, 2019 The Auto Tune Evo VST 6.0.9.2 demo is available to all software users as a free download with potential restrictions and is not necessarily the full version of this software. Compatibility with this pitch correction software may vary, but will generally run fine under Microsoft Windows 10, Windows 8, Windows 8.1, Windows 7, Windows Vista and Windows XP on either a 32-bit or 64-bit setup. Demo version of auto tune. Free Auto-Tune Demo downloads, free Harmony Engine Demo downloads plus free demo downloads for other Antares vocal plug-ins via the free AVOX Demo download. All product demos require an iLok USB key and an iLok account.
Enter the arguments to the add preshared command into the file on each system, as shown in the following substeps.
For example, on the enigma system, you would add the following keying information to the ike.preshared file:
On the ada system, you would add the following keying information to the ike.preshared file: